Ransomware Explained – The Cybercrime that has struck the HSE

By: Mark Hurley
Reading Time: 6 Minutes
Recently, the HSE – Irish Health Service Executive and the Department of Health – were struck with a Ransomware attack that shocked the country and made news all over. We’re looking to bring more information on how such attack was made possible and how you could protect your business from one. Keep in mind that small and medium organisations are the main targets for cybercriminals today, mainly because of their lack of awareness and protection.
In today’s article, we’ll be explaining what is Ransomware, how it happens, and a few basic methods to avoid it. If you’re looking for a full detailed guide including info on the best tools and procedures to protect your business, we have it in this link: What is Ransomware and How to Avoid it – The Complete Guide.
What is Ransomware
A successful ransomware attack can be devastating to a business. Organisations caught unprepared could be left with the choice between paying a ransom demand and entirely writing off the stolen data.
In our day-to-day cyber security practice, we perform many assessments with new and potential clients. Among this wide variety of professional companies, we find a very different understanding of the threat Ransomware poses to their businesses.
There are the unknowledgeable optimists that believe it will never happen to them. Clearly, this is not a recommended stance.
There are also the informed optimists that believe they have all angles of protection covered. That may or may not be the case. Assumptions can be dangerous.
Finally, there are the affected pessimists – the ones who have suffered from a Ransomware attack and for whom it may be too late. We receive calls from complete strangers asking how they deal with a Ransomware hit. We always ask the same two questions – do you have a backup, and do you carry Cyber Liability Insurance. The silence at the end of the phone can be deafening.
Whichever of these groups you belong to, it is vital to become informed and engage with preventative measures. That way, you can plan for the worst outcomes so your business can continue to thrive after such an attack.
The purpose of this article is to provide that information and to provide some of the measures required to both prepare and recover if your business is impacted by a ransomware attack.
Ransomware is a multibillion dollar criminal enterprise executed by Cyber Criminals to disrupt access to your systems, business, and personal information. It is a form of malware that encrypts a victim’s files. The attacker then demands a ransom from the victim to restore access to the data upon payment.

Once infected, the attackers demand a ransom (generally in Bitcoin) to liberate access to your data and critical business systems. Worryingly, this activity is on the rise at an exponential rate. Research suggests that in 2020 a new organisation was hit by a ransomware attack every 14 seconds and that Ransomware incidence increased 50% in Q3 in 2020 alone.
Adding insult to injury, the Cyber Criminals are leveraging the current Covid crisis to target vulnerable remote workers and infect susceptible organisations. Cybersecurity Ventures predicts that ransomware damage will exceed $20 billion by 2021. It is so effective because it takes many guises. You must be aware of all of them to protect your data and your entire network effectively.
Case Study: The NHS
The HSE attack was not the first time cybercriminals targetted healthcare organisations. A famous example of ransomware is the WannaCry attack of May 2017. This was a piece of malware that infected over 230,000 computers across 150 countries within a single day. It encrypted all files it found on a device.
WannaCry mainly affected large organisations. The National Health Service in the UK being one of highest profile targets affected. Surprisingly, the attack’s impact in the UK was lower than it could have been. Due to the fact it was stopped quickly, and it did not target extremely critical infrastructure, like railways or nuclear power plants. However, economic losses from the attack were still estimated to be over 90 million pounds for the UK alone and about 6 billion pounds worldwide.
Recently, 22 cities in Texas were hit with ransomware in September 2019. The attackers demanded $2.5 million to restore encrypted files, leading to a federal investigation. Moreover, ransomware is especially prevalent in financial and healthcare organisations, with cyber-criminals targeting 90% of these businesses last year.
How Does Ransomware Happen?
Ransomware begins with malicious software being downloaded by an unwary person through an infected email or link onto their computer or smart device.
Once Ransomware infects an endpoint, it will run free wherever it has access. In seconds, the malicious software will take over critical process on the device. Then search for files to be encrypted, meaning all the data within them is inaccessible.
The ransomware will then infect any other hard drives, network attached devices etc, taking out everything in its path – including backups.
This entire process happens extremely quickly. In just a few minutes, the device will display a message that looks like this:
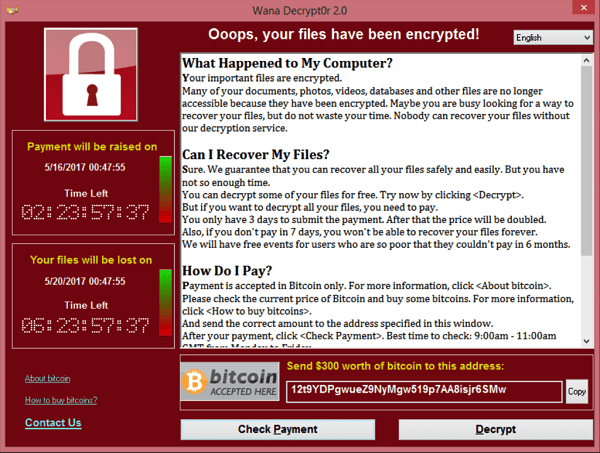
This is the message that displayed to users who were infected with the WannaCry ransomware attack. As you can see, it’s a ‘cyber blackmail’ note. Users are informed that they have been locked out of their files and must pay to regain access.
The people within your organisation are often your most significant security risk. The major issue here is a lack of awareness and staff education about security threats. Many people are unaware of what threats look like and what they should avoid downloading, leaving you open to risk.
There has been a massive growth in Security Awareness Training platforms, which train users about the risks they face online, at work, and at home. Awareness Training teaches users what a suspicious email looks like and the best security practices to follow to stop ransomware. Such as ensuring their endpoints are updated with the latest security software. Security Awareness Training solutions typically also provide phishing simulation technologies.
It may not seem obvious, but identity theft lies at the core of a lot of backdoor Ransomware attacks. Hackers use administrative and other accounts to gain a foothold in your core systems. Adding MFA – MultiFactor Authentication makes the possibility of elevating privileges and giving the attacker the keys to run ransomware without barriers. MFA comes free with most Microsoft 365 packages, and more in-depth solutions also exist that extend more granular protection to all devices in the organisation.
Continuing the use of End of Line hardware and software increases your risk heavily. Over time, attackers discover the security vulnerabilities that are widely released by larger corporations. Many organisations rely heavily on older computers/software that are no longer supported, meaning they are open to vulnerabilities. Organisational security policies often overlook hardware/software that is out of date.
This dramatically increases the organisation’s risk of falling victim to an attack. Keep your operating system and 3rd party applications patched and up to date to ensure you have fewer vulnerabilities to exploit.
Preventing and Stopping Ransomware
One of the most important ways to stop ransomware is to have strong endpoint security. A program that blocks malware from infecting your systems when installed on your endpoint devices (phones, computers, etc.). Just be sure that Ransomware protection is included when you’re searching for a security package, as many traditional Anti-Virus products are not equipped to defend against modern Ransomware attacks.
As ransomware is commonly delivered through email, email security is key in preventing ransomware. Secure Email Gateway technologies filter email communications with URL defences and attachment sandboxing to identify threats and block them from being delivered to users. This stops ransomware from arriving on endpoint devices, while blocking users from inadvertently installing malicious programs onto their machines.
How to Identify a Suspicious Email? Click here to learn more.
DNS Web filtering solutions stop users from visiting dangerous websites, downloading malicious files, and blocking ransomware spread through viruses downloaded from the internet, including trojan horse software. DNS filters also block malicious third-party adverts. Isolation technologies completely remove threats away from users by isolating browsing activity in secure servers and displaying a safe render to users. Moreover, Isolation does not affect the user experience. These solutions deliver high-security efficacy and seamless browsing.

Once a ransomware attack succeeds and your data is compromised, the best protection for your organisation is to restore your systems quickly and minimise downtime. The most effective way to protect data is to ensure that it is backed up in multiple places, including your main storage area, local disks, and a cloud-continuity service. In the event of a ransomware attack, backing up data means you will be able to mitigate the loss of any encrypted files and regain functionality of your systems. Cloud data backup and recovery is a crucial tool in remediating against Ransomware.
Learn more about Disaster Recovery in this article.
Reducing the risk and damage of Ransomware requires a mix of frameworks, policies, training, and technology. The best companies perform a detailed GAP analysis using a Cyber Security framework such as the NIST CSF in conjunction with security controls such as the CIS 20 controls. This approach leads to better outcomes, and it’s how we commonly proceed with our customers.
Feel free to get in touch if you have doubts or would like to learn more about protecting your business against cyber security threats. Our team of experts will be happy to offer advice and guide you through what an effective strategy looks like for your business.