Assessing Your Personal Risk of Identity Theft

Estimated Reading Time: 5 Minutes
This is the third article in our Identity Theft series. The first post worked as an introduction to identity theft, while the second explained how it happens, and the many security vulnerabilities that enable it. Please feel free to go back to those if you are looking for more information on this subject.
Alternatively, download our Free Essential Guide on How to Avoid Identity Theft to have all information in an illustrated PDF guide.
In this post, we are going to talk about you, and the online habits that could put you at risk of identity theft. Not only will we be revealing the kinds of suspicious activity that may indicate you have been targeted by a cybercriminal, but we will discuss why a strict password policy is crucial, and how to implement one. Finally, we have a simple self-test for you, to help evaluate your own personal cyber security.
Data Leaks prompt Identity Theft
Major company data breaches have occurred over the past decade, where even the most cautious user could not have avoided having their information leaked. Yahoo alone has suffered data breaches that have exposed the personal information of all of its 3 billion accounts. When we add in other major data breaches of the last three years, the total comes to over 4.3 billion cases. Dropbox, eBay, and LinkedIn were among the high-profile targets.
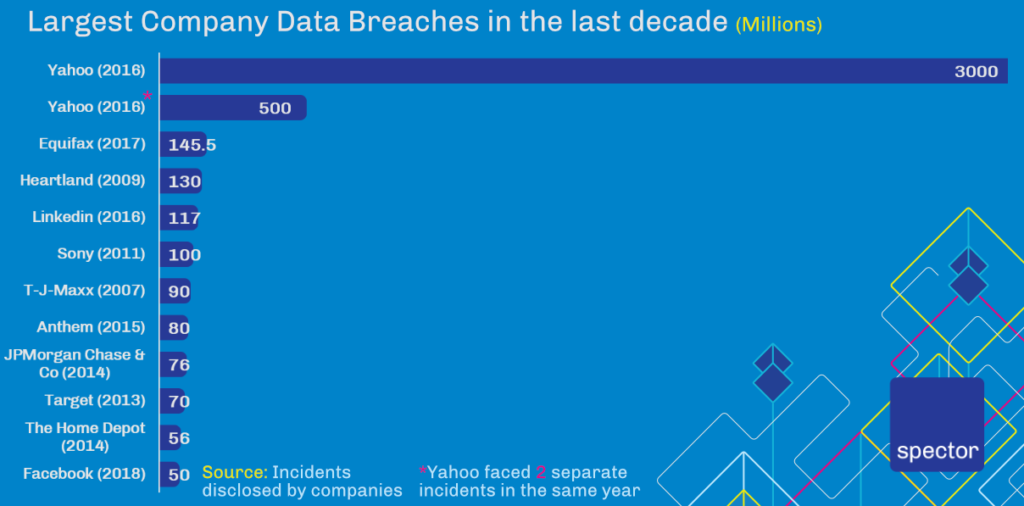
If you are looking for more information on Data Breaches, view this detailed Infographic by Hosting Tribunal, highlighting the 15 biggest cases in 15 years.
Any of these data breaches could have exposed a user’s personal data to a cybercriminal, which could then be used as the initial seed of identity theft. Remember, it only takes one piece of critical personal information in the hands of a cybercriminal to put you at risk personally.
We recommend using this online tool to check if your credentials have been leaked. If you have been the victim of some of the circumstances above, you could use this site to verify if your identity is available for criminals to take.
Suspicious Online Activity and Its Implications
Although identity theft primarily takes place online, many of the initial signs that you have been targeted will become apparent in the real world. Indeed, the symptoms of identity theft often do not occur until after the data breach has already occurred. The cybercriminal will have spent some time selling your identity on, and then the perpetrator of the crimes will carry them out. All of the suspicious activities below could indicate that you have been the victim of identity theft. If two or more of these things happen, you can be certain you have.
- You spot banking or debit/credit card transactions that you don’t recognise, or strange payments being sent from services such as PayPal, Skrill or Neteller.
- You realise that you are not receiving all of your usual snail mail, such as bills, etc.
- Online or real-world payments are declined when you use your debit/credit card to pay.
- Your personal credit report shows loans or other types of credit that you never applied for.
- You are contacted by a collection agent to chase you to pay for something you did not buy, or to make loan or credit repayments for financial products and services that you did not apply for.
- One of your insurance policies such as medical or motor insurance fails to allow you to claim due to missed premium payments.
- The records of your health plan activity show treatments for an injury or illness you never suffered.
- You receive communication from a previous employer, telling you that they may have exposed your personal data to theft.
- You start to receive emails from online vendors, recommending that you take advantage of an upgrade offer, or a discounted addition to goods or services you never purchased online.
A Strict Password Policy Helps
We have all been guilty of using a weak password at one time or another. If you use multiple websites regularly, it can be very tempting to use the same simple password for every site to make things easy. Of course, this is a terrible idea in relation to your online security. Establishing a strict password policy is your first line of defence against hackers. Always make sure that:
- You always use a password of more than 8 characters
- You use lowercase, uppercase, numbers and symbols in every password.
- You do not use the same password for more than one site.
- You do not keep a note of your passwords, or some type of hint document to help you remember them.
- You don’t use passwords that are easy to guess – birthdays, obvious dates or names that are important to you.
- You never share your passwords with anyone.
- You change your passwords regularly.
We have a complete guide on How to Create and Manage Passwords, available on our website. Check it out if you want to learn the best techniques to create strong passwords that are easy to remember.
If you have not been using such a password policy, and you start to notice strange activities such as those mentioned in the section above, change your passwords using such a policy ASAP.
A Password Manager is a very useful tool that will generate strong passwords and keep them safe for you, behind an encrypted barrier. There are many of these available on the web or app stores.
Your Identity Theft Self-Test
In this section we have a short identity theft self-assessment test you can work through, to discern your own personal level of risk. Answer each question with a yes or no.
- 1. You check your credit report regularly.
- 2. You check your bank and credit card statements, against credit/debit card receipts.
- 3. You know the approximate billing cycles of your credit cards, loans and other financial services and can spot a discrepancy.
- 4. You destroy personal documents before you throw them away.
- 5. You destroy all of your household mail such as utility bills before you throw it away.
- 6. Your snail mail is delivered to a locked, secure mailbox.
- 7. You post your snail mail at the post office, and not in a public post-box.
- 8. Your mail is collected and held by a family member or friend while you are away.
- 9. You do not take part in internet surveys, or other requests for information.
- 10. You keep important data and documents safely located at home.
- 11. You do not carry all of your credit cards and chequebooks at all times, only the ones you need.
- 12. Any paperwork you have to submit to an organisation, such as your employer, has personal information that they do not need to see blanked out.
- 13. You think twice before you post anything on Social Media or your personal blog.
- 14. You do not use a weak password.
- 15. You do not use the same password for your online accounts.
- 16. You change your passwords regularly
- 17. You have multi-factor authentication enabled for your online accounts.
- 18. You have an Anti-Virus or Anti-Malware software active on your devices.
- 19. You do not open e-mail attachments or links from strangers.
- 20. You always confirm with a person if they are asking you to perform any money transfer over e-mail or social media.
- 21. You are generally security conscious, and regularly take common-sense driven actions to protect your personal information.
If you answered no to:
14 or more questions – your Identity is in danger;
9 to 14 questions – a lot to improve;
4 to 9 questions – good, aware of the main risks;
3 or less – excellent, vigilant.
Always remember that you are the first line of defence when it comes to your own cybersecurity. Acting in a safety-conscious manner at all times is the best way to deter cyber criminals and keep your identity safe from identity theft. Hopefully, you are becoming an expert in Identity Theft. Our next blog post will tell you what to do if your identity has been stolen, a question that we hear a lot from our customers.
To have all this information in one place, including exclusive methods, data and tools to avoid Identity Theft, download our Essential Guide. It’s an illustrated PDF with all the knowledge you and your staff may need to avoid facing this threat.