Developing an Action Plan to Address your Technology Risk
Estimated Reading Time: 7 Minutes
In this article, you will learn about the crucial components to consider when creating an Action Plan to address technology risk. In reality, even though technology risk has plenty of complexities and details, the logic behind the action plan should be quite similar to the one guiding a standard risk management plan.
Serious about managing technology risk? Our best recommendation:
Building a system leveraging the NIST framework to manage risk
How is Technology Risk Evolving
Technology risk is ever-changing and intricate, and it cannot be ignored. In today’s world, the odds of facing technological disasters is higher than the ones from the natural world, and the consequences could be just as disastrous. Loss of critical business data and equipment, staff unable to operate, customers unable to buy – the more dependant you are on technology, the higher the risks.
That being said, there is no reason to panic. Once you have an idea of your main assets and the risks you could be facing, you can begin to tackle them by order of priority. If you haven’t yet identified them, you can start by reading Building an Asset and Risk Register. There you can find a sample Risk Register and more useful information, so check it out and come back when you’re ready.
Leveraging the Risk Register to define your Prioritised Plan of Action
The key result from establishing a full Risk Register is that your core and most critical risks rise to the top for all to see. Your plan is now to define how to handle these risks.
Firstly you need to understand your inherent risk and to assess the consequences and likelihood of failure. If the inherent risk is high, with damaging effects, you need to treat that risk by applying a control and reducing it to a tolerable level. However, that is not your only option.
Every company can adopt different methods for addressing IT Risk. For example, some qualitative and others quantitative. In our practice, we use the NIST CSF approach to get most organisations advancing, and an ISO 27001 approach for the ones looking to maintain a higher level of compliance, such as financial services or healthcare.
Let’s take a look at the options open to you as the Risk manager with some examples that will hopefully allow you to understand how to manage your risks.
Option 1 – Employ controls to mitigate risk
A control gives you the ability to change the inherent risk outcome. For example, you may decide that you cannot afford to lose any more than 1 hour of data from your core business system (ERP) as recovering that would be an operational nightmare.
You can apply a control such as a more frequent backup of the system – say to 15-minute windows. In this case, the control already existed and just needed to be altered to address the risk of data loss.
For the sake of comprehensiveness, three types of security controls will assist in mitigating risk:
- Management controls: The security controls that focus on the management of risk and the management of information system security.
- Operational controls: The security controls that are primarily implemented and executed by people (as opposed to systems).
- Technical controls: The security controls that are primarily implemented and executed by the system through the system’s hardware, software, or firmware.
It is the combination of all three types of controls that provide robust security. In our example above we have a Disaster Recovery Plan (management control), that is managed by your internal or external IT resource (operational control), and backup and recovery software/ hardware systems deliver the ability to recover (technical controls).
A common problem with control adoption is that they often make systems less simple to use. When usability is an issue, many users will attempt to circumvent security controls; for example, if passwords must be long and complex, users may scribble them down.
Balancing security, functionality, and usability is often a challenge. The goal should be to strike a proper balance: provide a reasonably secure solution while offering the functionality and usability that users require.
Option 2 – Transfer risk
Risk transfer is a risk management strategy that involves the shifting of an identified risk from one party to another. The simplest example, of course, is the purchase of an insurance policy, by which a specified risk of loss is passed from the policyholder to the insurer.
In terms of IT Risk, there are new Cyber liability policies that provide first-party cover as well as a host of additional benefits (legal, HR, PR advice) that allow an organisation to offset operational and reputational risks.
Option 3 – Cease risky activity

There is always the option to cease a risky activity altogether. It is not uncommon to accept the status quo of how things have always been done even when those activities expose you to risk.
With the arrival of GDPR, we have advised many clients on how they share information both within and outside of their organisations. It has meant that they now have entirely ceased the sending of personal data through unsecured means. They have sought different ways of moving that data or changed processes to suit the security requirement.
Option 4 – Accept the risk
Risk acceptance means accepting the identified risk and not taking any other action to reduce it because you can admit the potential consequences. For example, you may decide to accept a risk because the cost of eliminating it ultimately is too high. If you choose to take a risk it is a good policy to qualify and support that opinion.
An Auditor may not see this the same way that you do so it is essential to be able to stand over your reasoning.
Ownership, Accountability and Frequency
Although Risk Registers are unwieldy, they do provide the beginnings of a system and discipline around the assessment and ownership of your IT risks. This allows you to calendarize and set an agenda for review in place. Auditors are invested in seeking out evidence that you are doing the right thing.
They want the evidence from logs and activities, to how you manage your approach to IT Risk. Moreover, they are looking for accountability – someone has to own the risks.
This evidence-gathering process is a crucial part of the risk management system, and it should happen in parallel with your actions to mitigate risk. Keeping track of your efforts will make your life much more straightforward in an audit and bring precise accountability on what has and hasn’t been done.
More information on this can be found in the article:
Before the Audit – Gathering Evidence to Prove Compliance
Scorecard
A Scorecard is an excellent way of measuring your progress and assessing the main topics that need to be developed in every year or quarter. At Spector, we’ve been using scorecards with customers for many years, and their indications always bring much more clarity to reports and the action plan.
The simplest way to measure your score is to leverage an existing classification and scoring system and evaluate how your business is doing. We recommend utilising the NIST Cyber Security Framework, as it covers the most important areas of technological resilience and risk, with the added benefit of being incredibly easy to understand and present to the board.
As you address your risks and improve your cyber security maturity levels, you will be able to update your scores on your NIST profiles under the 5 key functional areas of Identify, Protect, Detect, Respond and Recover. Each of these areas has a number of categories and subcategories, which you can use to assess your level of cyber resilience. Depending on how well your business is, you could fit in one of the 4 tiers of implementation.
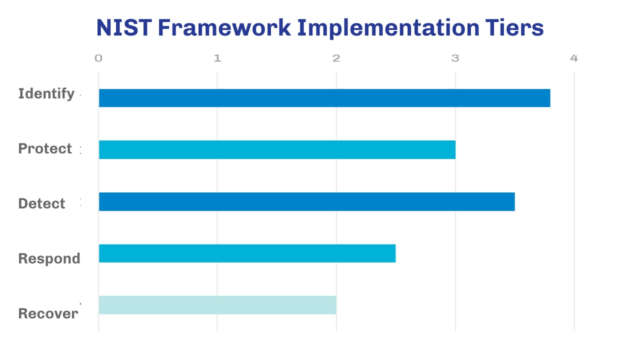
As you advance and tackle technical risk, your score should increase in each of the areas and bring you to a new tier, according to what your target profile and priorities are. Make sure to keep this up to date and celebrate your progress.
For more detail in how to leverage the NIST framework to tackle technology risk, read:
The Guide to NIST for Financial Services Organisations
To get you started, we have developed a simplified Self Assessment Tool that you can use to evaluate your business and identify your current and target profile. By using this tool, you should be able to have a better practical understanding of how useful NIST can be. Keep in mind that it doesn’t cover all bases normally addressed by the framework, especially since we have shifted it from a levelled approach (1-4) into a “yes or no” approach to keep things simple.
In the following chart, you can see the starting profile, current working profile – i.e. as it is today or at last review – and target Cyber Security profile, based on the 5 functional areas of the NIST Cyber Security framework. The tool gives a simple view of how you are progressing your Cyber Security maturity levels.
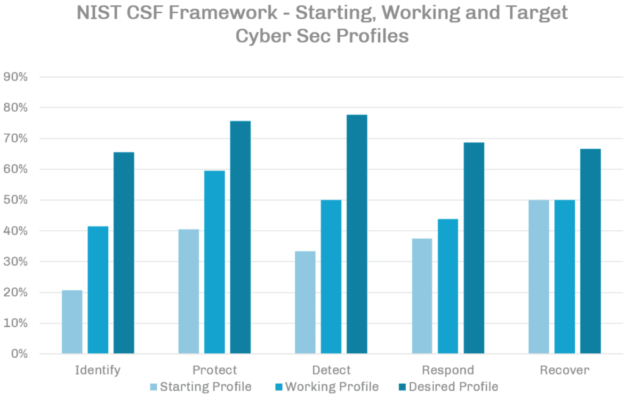
These tools and knowledge should help you define a clear path to begin addressing your risk. Not only that, but you will be able to prioritise actions and understand where your business is improving and where it still needs to improve.
Continue Tackling the Risk – After the Action Plan, prepare for the Audit
The next part of the series that we will discuss is about Evidence Gathering – which, as discussed above, means maintaining data that proves you are being compliant and improving your practices. It is a process that should happen in parallel while you are executing your action plan, and it will make your life much more comfortable during an audit.
For more tips and advice on how to present your progress to an auditor or the board, read: Preparing for an Audit – how to tackle cyber security and discuss it with the board.
As always, talk to us if you need specialised assistance. A reliable IT and Risk Management system will provide your Action Plan with the attention it deserves. At Spector, we specialise in technology risk management and have the tools and experience to make this process look simple.
Thank you for reading! Follow us on Social Media for more exclusive content. If you have found value in this content, please share it with others who may feel the same way. Be sure to leave a comment below if you have any queries or feedback about this topic.

