Preparing for your Cyber Security & GRC Audit

Estimated Reading Time: 9 Minutes
Welcome to our series of articles on Managing Technology Risk and Governance. In this chapter, we will investigate how to prepare for a Cyber Security audit and prepare comprehensive reports for the board. These are recommendations based on our audit and board reporting experience over 15 years. Being ready for it is key to saving time and effort.
The core fundamentals of a cyber security audit are no different from a traditional audit. The auditor will be looking for anything that is out of place and your business has to prove that it is following best practice and addressing any issues. Audit experience is useful in both scenarios.
Adopting a framework prior to an audit can be extremely beneficial, as it will provide your business with direction and illustrate what are the standards and best practices you should be pursuing. Here at Spector, we recommend leveraging the NIST Cyber Security Framework to succeed in your GRC efforts. To learn more about it, read our Guide to NIST for Financial Services.
What is the purpose of a Cyber Security Audit
A cyber security audit is a vital process for identifying fundamental weaknesses in your company’s tech infrastructure. These assessments help you verify what lives inside your network, what needs to be protected, and how to improve protection. Auditors are looking for proof that you are doing the right thing and improving. It is not a name and shame process; audits exist to help you grow.
However, as relevant as cyber security audits are, many companies are not very well prepared for them. So, how can you prepare for a cyber security audit so that it can be completed quickly and efficiently?
If time is in your favour, one of the best approaches you could take to succeed on this is to gather and store evidence of your activities. By doing so, you can quickly prove to an auditor that you have been compliant and all main risks have a control and an owner – which shows accountability. For more detail on this, read the article: Before the Audit – Gathering Evidence to prove Compliance.
Moving to a closer date to the audit, there are a number of things you can do to prepare apart from gathering evidence. Here is a short list of the main tips to help you get ready:
Create a Diagram of Your Network Assets
While part of the goal of any audit is to identify potentially unknown assets on your business network, giving your auditor a network diagram can help them save time and get a head start on their assessment. A network diagram outlines the overall structure of your network—what assets are present, how they’re connected, and how they are linked. Many tools exist today that can provide a real-time view of your network assets. These make the process of gathering data simpler than drawing diagrams that go out of date as you finish them.
Verify with the Auditor Which Stakeholders They Need to Talk to

At one point, the auditor will need to speak to subject matter experts within your organisation to get a complete picture of your cyber security policies and architecture. So, before the audit begins, ask the auditor which of your key stakeholders they will need to talk to during their inspection, and set aside some time for these stakeholders to attend a meeting and what tools or access they may need during their audit.
Build Your Cyber Security Policies into a Single, Easy-to-Read Book
While your auditor will likely conduct interviews of your staff to get a feel for their grasp of security, it can be helpful for them to have access to your cyber security policies during their audit. Here, taking all of the documentation regarding your business’ cyber security policies and procedures and organising them into a single book can be massively helpful.
Spector provides a book of 20+ cyber security policies as well as other key business documents that we build into a single policy book. We also include evidence in these documents – which will likely be asked for. Some examples include:
- Password policies
- User Access Controls
- Acceptable Usage Policies
- Backup and DR Policies
- Incident Management Procedures
- Data Mapping Processes and many more.
- Cyber security training logs
This policy book helps the auditor understand your organisation’s overall cyber security awareness as well as spot potential gaps in your security policies and procedures that need to be addressed.
Study Up on All Applicable regulatory and Compliance Standards Prior to the Audit
Most organisations have one or more compliance or regulatory standards that they strive to meet, such as PCI DSS, GDPR etc. In 2016 the Central Bank of Ireland released the “Cross-Industry Guidance in respect of Information Security and Cyber Security Risk”. It is a fantastic resource – albeit a little dated – on recommendations of what may be expected at audit time.
By educating yourself about your compliance requirements, you can put yourself in a position to work more collaboratively with your cyber security audit & compliance team as well as verify that the suggestions they make are realistic and positive.
Define the Project Scope with the Auditor
One of the most vexing problems companies face is determining the scope of an audit and how to prepare for the review. Without a scope, lags are inevitable because there are always unforeseen events that can disrupt outcomes, your time and costs. An experienced auditor should be able to anticipate these events to some extent and inform you (to some degree) of their requirements in advance.
When discussing project scope for an audit, be sure to ask questions about why the auditor needs certain resources, or if there are any resources they require that you haven’t provided yet. Get details about why specific assessment steps are necessary and what they entail. Be confident!
After the Cyber Security Audit Starts
When the auditor begins making their assessment of your organisation’s cyber security infrastructure, be sure to ask them to bring any significant issues to your attention as soon as possible. No-one needs surprises at the conclusion of the audit. This also gives you a chance to start remediating these issues as soon as you can.
Also, be sure to take any alerts from the auditor seriously and ask for suggestions about how you can fix these issues. Many experienced auditors are familiar with numerous cyber security tools and quick fixes for common problems that you can implement very quickly. However, they may want to complete their full audit before making some recommendations so they can suggest the most comprehensive solution possible.
Dealing with the Board

Concerning the board, our advice is to keep it simple. There are often over 20 items to be discussed at a board meeting. You have a short time window in which to get your point across – and possibly ask for investment.
Educating the board about the relevance and role of the tech infrastructure of your business is a good place to start. We recommend reading the document mentioned above; the Central Bank Guidelines in respect of IT and Cyber Security Risks. The report is easy to read and highlights the main requirements and risks of a regulated firm. After introducing them to the topic effectively, your job will be much more straightforward.
Another strong recommendation for this subject is to consider adopting a framework such as the NIST Cyber Security Framework. It covers 5 key functional areas that are imperative for a robust Cyber Security strategy – Identify, Protect, Detect, Respond, Recover. In short, this framework comprises of several relevant practices, ranging from user training to backups and security tools. It is simple enough to be quickly presented to the board while holding all details under the surface.
The following insights will also be valuable in transmitting your message in the best way possible.
Guiding principles for board reports
- Relevant: Relevant to the audience (full board; key committee)
- Reader-friendly: Use summaries, callouts, graphics, and other visuals, avoid technical jargon
- Meaningful: Communicate insights, not just information.
- Highlight changes, trends, patterns over time
- Concise: Avoid information overload
- Discussion: Reports should also enable dialogue and debate.
- Continuous improvement: Review the format and content regularly.
Key questions to help identify and develop cyber security metrics
What metrics do we have that indicate risk to the organisation? Boards need to know that the organisation’s critical assets are being protected.
One advantage of utilising the NIST Cyber Security Framework is that it provides the board with an easy-to-understand scoring system based on 4 tiers. As you advance and tackle technological risk, your score should increase in each of the areas and bring you to a new tier, according to what your target profile and priorities are.
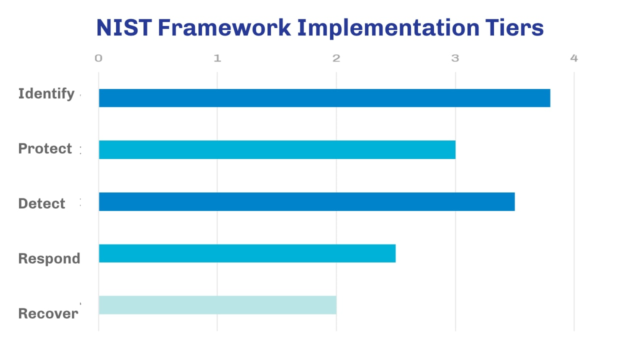
For more information on these tiers and on how NIST works, read:
The Guide to NIST for Financial Services Organisations
Moving on, independently of what framework you are using, these are the main questions you should be considering:
What investments are necessary for cyber security?
Organisations need to understand their current and future cyber security needs before they decide what investments will drive down risk. Useful questions include:
- What initiatives were not funded in this year’s budget, and why?
- What trade-offs were made?
- Do we have the right resources, including staff and systems, and are they being deployed effectively?
How do we measure the effectiveness of our organisation’s cyber security programme and how does it compare to those of other organisations?
Board-level metrics should highlight changes, trends and patterns over time, show relative performance, and indicate impact. External cyber security specialists may be able to provide useful comparisons within industry sectors.
If you are leveraging the NIST Framework, you can easily visualize your progress in all key functional areas. The best way to do it is by keeping track of your initial profile and comparing it to your current and target profile, just as seen on the chart below:
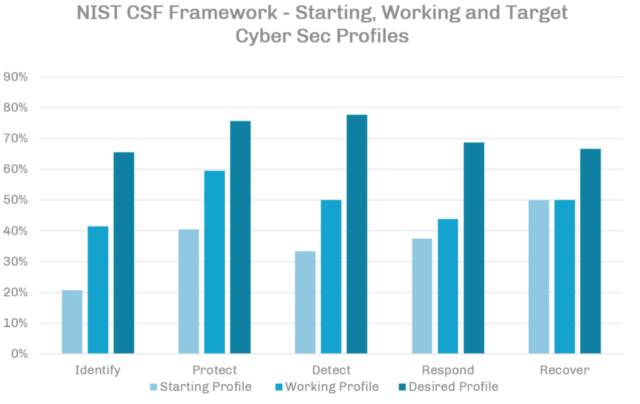
To give you an idea of your current NIST profile, we have developed a simplified Self Assessment Tool that you can use to evaluate your business and identify your current and target profile. By using this tool, you should be able to have a better practical understanding of how useful NIST can be. Keep in mind that it is a simplified version of the framework and it doesn’t cover all bases normally addressed by the full scope.
How many data incidents (e.g. exposed sensitive data) has the organisation experienced in the last reporting period?
This metric will inform conversations about trends, patterns and root causes. Remember to reinforce the fact that incidents are bound to happen – it’s not a matter of “if”, but “when”. How effectively the organisation reacts to these incidents is the primary point of discussion.
How do we assess the cyber-risk position of our suppliers, vendors, JV partners and customers?
Supply chain relationships typically pose increased risk for organisations given the degree of system interconnectivity and data-sharing that is now part of everyday business operations. Useful questions include:
- How do we conduct ongoing monitoring of third-party risks?
- How many external vendors connect to our network or receive sensitive data from us?
What metrics do we use to evaluate cyber security awareness across the organisation?
People are often the biggest cyber security threat for many organisations. Data about policy compliance and the implementation and completion of training programmes will help inform conversations about insider risks.
Using these Insights to be Audit-Ready
Throughout this content series, we have provided you with the tools and knowledge you will need to perform much better in this stage. This knowledge is based on years of experience operating in many regulated industries and having internal lead-auditing capabilities.
It’s the material we wish we had when we were starting.
The pieces of content you have will aid you in understanding your risks, assessing your vulnerabilities, prioritising and acting on them. The material can give your business a significant edge in this aspect, and you should use it as a competitive advantage.
If your objective is to get audit-ready and increase your organisational maturity, you must be in a much better place by now. However, to have your business ready for the future and secured against evolving risks, you still have to develop an evolving system.
Building a Risk Management System – Simplifying the Process
Here at Spector, we have two basic service offerings in this area: the Gap Analysis and the Cyber Security Programme.
We usually recommend companies to begin with the Gap Analysis, as it will provide us with more knowledge of your setup and a clear direction for your needs. This service consists of a project to analyse and identify the most critical vulnerabilities in your structure. It can be done in a short period by our team, causing minimal disruption. To learn more about how it works and what is involved, read our Gap Analysis brochure, available on this link.
The Cyber Security Programme, on the other hand, is the following step after the Gap Analysis, and it will address the actual mitigation of your risks and development of your structure on a continuous basis. We will lay our tools and resolve the most urgent issues, to then initiate new projects to reach your business goals. This allows us to close the gap between desired and current state. If you want to learn more about this stage, we have information available on this link.
Both solutions will help turn this daunting process into an automatic and uncomplicated job. If you have questions, feel free to Book a Call with us. We will be happy to learn about your challenges and figure the best solution.
Thank you for reading! If you have found value in this content, please share it with others who may feel the same way. Follow us on Social Media for more exclusive content.