Understanding and Calculating Organisational Risk

Estimated Reading Time: 5 Minutes
Written by Aaron Nolan
Understanding organisational risk is crucial not only for a risk manager handling GRC (Governance, Risk and Compliance) but also to any business owner or member of the C-Board to future proof their companies and ensure Business Continuity.
In this article, we will be addressing some of the most common doubts and providing the essential information you will need to understand the nature of risk. With this knowledge, you can begin developing tactics to shield your business against it.
What is Risk?
Risk deals with the possibility or likelihood of a situation occurring based on the threats and vulnerabilities of an asset. Both vulnerabilities and threats can be mitigated using security controls, but we must understand the level of exposure first.
- A threat: to your business is any likelihood of unwanted potential harm. An example of a threat might be a thief or a computer virus.
- A vulnerability: on the other hand, is a weakness or absence of a safeguard in an asset. An example of a vulnerability is a broken alarm system or an unpatched server.
Once all the threats and vulnerabilities have been calculated, you will find your Total Risk. This is the organisation’s exposure level before implementing any mitigation controls. Being aware of all your risks is crucial to conduct a Business Impact Analysis.
Risk Assessment vs Risk Analysis
Many people use these two phrases interchangeably, but they are two separate things. A risk assessment is used to gather the data about the company, like its assets register, asset value and data flow. The risk assessment is used to understand the scope of the business and its potential exposure.
A risk analysis, on the other hand, is used to calculate the probability of a vulnerability being exploited. An organisation should list all probable threats and vulnerabilities to the gathered data from the assessment, in a process called Threat Modelling.
This should be used to produce a Gap Analysis or a Risk Mitigation plan, which will generate a list of risks that can be acted upon based on a cost versus benefit analysis. Therefore, a Risk Analysis must follow a Risk Assessment.
For more details and useful tools to help you build your Asset Register and Risk Register, read: Building your Asset and Risk Register to Manage Tech Risk. There you will find a sample risk register and a webinar with detailed instructions on how to use it.
Calculating your Risk
After your organisation has completed the threat modelling process, there are some ways they can calculate its risk. Depending on the type of risk and type of potential damage that could be caused, one way may be more suitable than the other. In this article, we’ll be exploring Quantitative and Qualitative risk analysis.
How much does downtime cost your organisation? Find out with our Downtime Calculator
Quantitative Risk Analysis
A Quantitative Risk approach adds costs or monetary value to the risk allowing you to easily see a cost-benefit analysis of any mitigation process.
For a Quantitative Risk analysis to work, each asset must have an asset value (AV) attached to it. By carrying out threat modelling, we will calculate the likelihood and consequence of a threat or vulnerability occurring.
By scoring your “likelihood” on a scale from 0 to 5, with 0 being highly unlikely to happen and 5 being certain to happen, this will give you a number to work off. Similarly, this can be done with “consequence”, with 0 being no effect on operations and 5 being a complete stop of operations.
These two numbers added together will give you a total amount which you can compare with your risk table. Example below:
|
Risk Level |
||
|---|---|---|
| Totally Acceptable Risk | Low | <=5 |
| Acceptable Risk | Medium | 6 |
| Transferable / Mitigatable Risk | Medium | 7 |
| Must Mitigate Risk | Medium | 8 |
| High Priority to Mitigate Risk | High | >=9 |
This number will give you your exposure factor (EF). The Asset Value (AV) times the Exposure Factor (EF) can be used to give the organisation the Single Loss Expectancy (SLE) of any threat occurring or vulnerability being exposed.
AV x EF = SLE
An organisation can use the Single Loss Expectancy (SLE) times the Annual Rate of Occurrence (ARO) to get the Annual Loss Expectancy (ALE) of a risk occurring.
SLE x ARO = ALE
By comparing the results of different threats and vulnerabilities, you should be able to understand which risks are more relevant and justify it to the board. By putting the results together into a chart, it becomes easy to visualise and compare risks, as seen below.
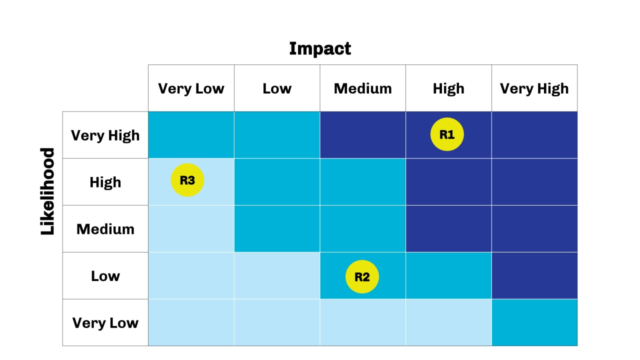
Knowing how to report these topics at a board meeting is also a vital part of the Risk Manager’s role. That could be especially hard if addressing Cyber Security risks. Should you need any help with it, read Preparing for an Audit and Discussing Cyber Security with the Board.
Qualitative Risk Analysis
Not all risk is tangible, therefore putting a cost on every asset may not be viable. In this case, an organisation should use a Qualitative Risk approach to review risk which might affect the reputation of the company.
A qualitative approach is a lot simpler and focuses more on business-critical operations than cost. It’s based on a subjective analysis, which can be done by scoring the risks of your assets as low, medium and high based upon the criticality to the business. This will give you a quicker indication of the required protection methods that need to be in place.
There are many different techniques and tools an organisation can use to calculate its qualitative risks like the Delphi technique, brainstorming or storyboarding.
Some organisations use a mixture of Quantitative and Qualitative risk analysis to cover both tangible and non-tangible assets. This is a very mature approach and safeguards the organisation both financially and reputationally.
Next Steps in Understanding and Addressing Risk
It is vital that the governance structure of an organisation understands the risks to their company to realistically implement controls to mitigate the risk. It is the responsibility of the organisation’s board members, C-level and stakeholders to understand the risks to their company.
The entire organisation must be examined in the Risk Assessment and Analysis process. The assessment must identify all assets and their value to the organisation, as discussed in detail in this article. The Risk Analysis process will evaluate the probability of a threat or vulnerability being exploited.
During the risk analysis process, the organisation’s governance structure should ask itself, “what will it cost us if we do nothing?” The Total Cost of Ownership (TCO) is the total cost of implementing a safeguard, and this must match a Return on Investment (ROI) for the controls. Otherwise, alternative plans for mitigating the risk should be considered.
There are different ways to address or mitigate risks, and we discuss them in more detail in our article Developing an Action Plan to Address Technology Risk. Before deciding to tackle threats directly, the organisation must determine the business impact of these exposures and identify the cost versus benefit of the mitigating controls.
Risk Management is a complex topic, so help yourself with our series of content and tools available in our blog.
If you need specialised help to guide you through this process, Book a Call with us. We have the expertise, the tools and the systems to make the risk management process simple and automatic.
Thank you for reading!
Follow Spector on our Social Media channels for more exclusive content.
![]()
![]()